Black Hat USA 2012 update
This year we have presented our jemalloc exploitation research work at Black Hat USA 2012, the leading information security conference. Our researchers Patroklos Argyroudis and Chariton Karamitas visited Caesar’s Palace at Las Vegas, Nevada and delivered the talk.

Our presentation was titled “Exploiting the jemalloc Memory Allocator: Owning Firefox’s Heap” and described in detail attack primitives against jemalloc and how these can be used to exploit heap overflow and use-after-free vulnerabilities that affect the Mozilla Firefox browser.
Specifically, the presentation was divided into three parts. The first part comprised of an introduction to the jemalloc memory allocator and presented its architecture, its fundamental concepts and its management data structures.
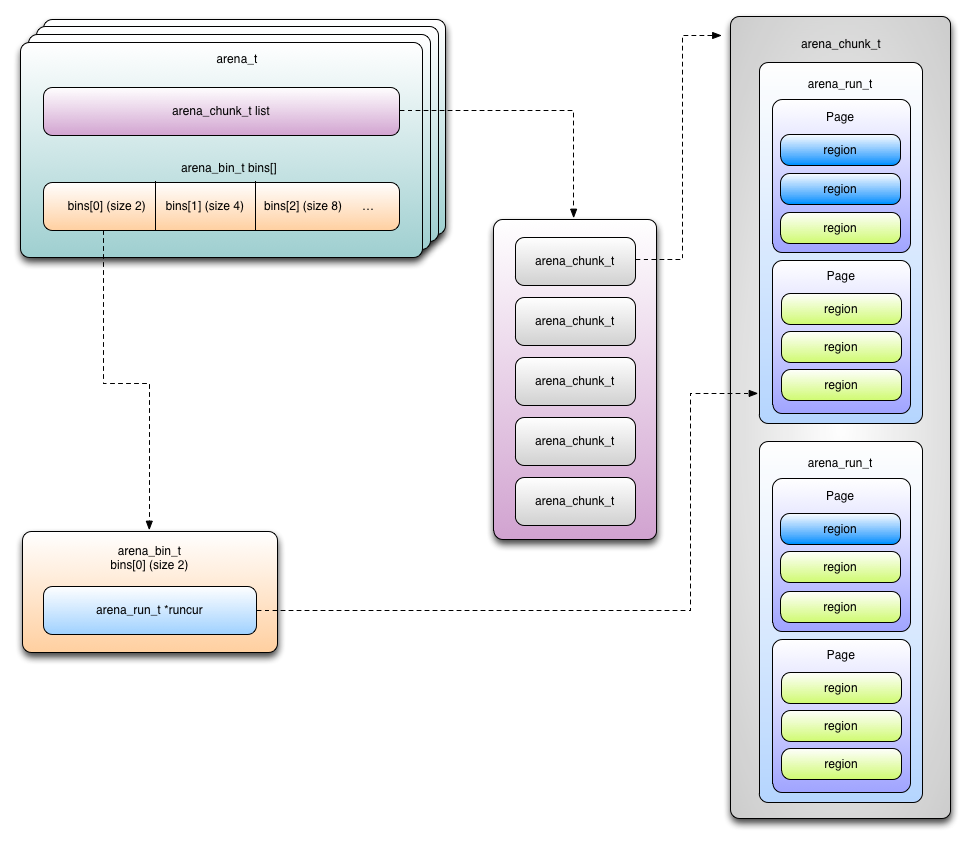
The second part of the presentation focused on identifying attack vectors against the allocator and on the development of novel exploitation approaches and primitives that can be used to attack jemalloc heap corruption vulnerabilities.
In the third and final part, our researchers applied these primitives to manipulate the heap of the Mozilla Firefox browser and to develop a PoC exploit for vulnerability CVE-2011-3026 (demonstrated on Firefox). Furthermore, a utility (unmask_jemalloc) was released that can be used to aid the process of exploit development for jemalloc/Firefox vulnerabilities.
Our presentation was 1 of 5 selected to be part of the “Breaking Things” track of the Black Hat conference. After the talk, our researchers participated in the press conference for the “Breaking Things” track and answered questions related to the impact of the presented work and its consequences.
Updated Presentation Material
All material from our presentation are provided below in the hope that they will be useful to security researchers willing to continue our work.
- Slides: bhusa-2012-slides.pdf
- Code archive: bhusa-2012-src.tar.gz
The development of the released code and utilities will continue on GitHub at the following repositories:
See you at the next security conference!
