Operationalizing Confidential Computing: Verifiable Attestation in Practice
IDC’s November 2025 white paper [1], based on its July 2025 study of 600 global IT leaders, shows that confidential computing has moved beyond early adoption. 75% of organizations are already using it, with 18% in production and 57% piloting, and participants are directly involved in systems that process confidential or regulated data.
This momentum reflects a concrete security gap. Traditional controls protect data at rest and in transit, but there is still exposure when data is actively processed. For most workloads, that means sensitive material is handled by compute and privileged software layers that are difficult to fully constrain. Confidential computing addresses the data-in-use gap by running computation inside hardware-based, cryptographically attested trusted execution environments (TEEs), complementing storage and network encryption to support end-to-end data protection.
Adoption has reached scale
Enterprises are processing more sensitive information in more distributed, multi-party systems. IDC notes that 44% of organizations need privacy-preserving ways to process sensitive datasets. This is exactly the kind of use case where confidential computing can reduce exposure without blocking collaboration.
AI-driven workloads and deployment realities add complexity. Study reports confidential computing usage across:
- Public cloud (71%)
- Hybrid or distributed cloud (45%)
- Private or on-premises (36%)
That means most teams are not designing for one cloud or one secure HW type. They are designing for variation: different hardware and TEE types, evidence formats, trust anchors, lifecycle events, and operating models across environments.
Enabling a confidential VM or container is a strong first step, but it is not sufficient on its own. A workload can run inside a TEE and still be unsafe if you cannot reliably verify its state, gate keys and sensitive data on that verification, while keeping those checks valid over time.
The bottleneck: validating attestation chains at scale
IDC’s key message for practitioners is that the hardest problems are about "how", not "why". The top adoption hurdle is validating attestation chains of trust (84.5%), followed by lack of skilled personnel (74.7%) and inconsistent public cloud approaches that drive vendor lock-in (68.2%).
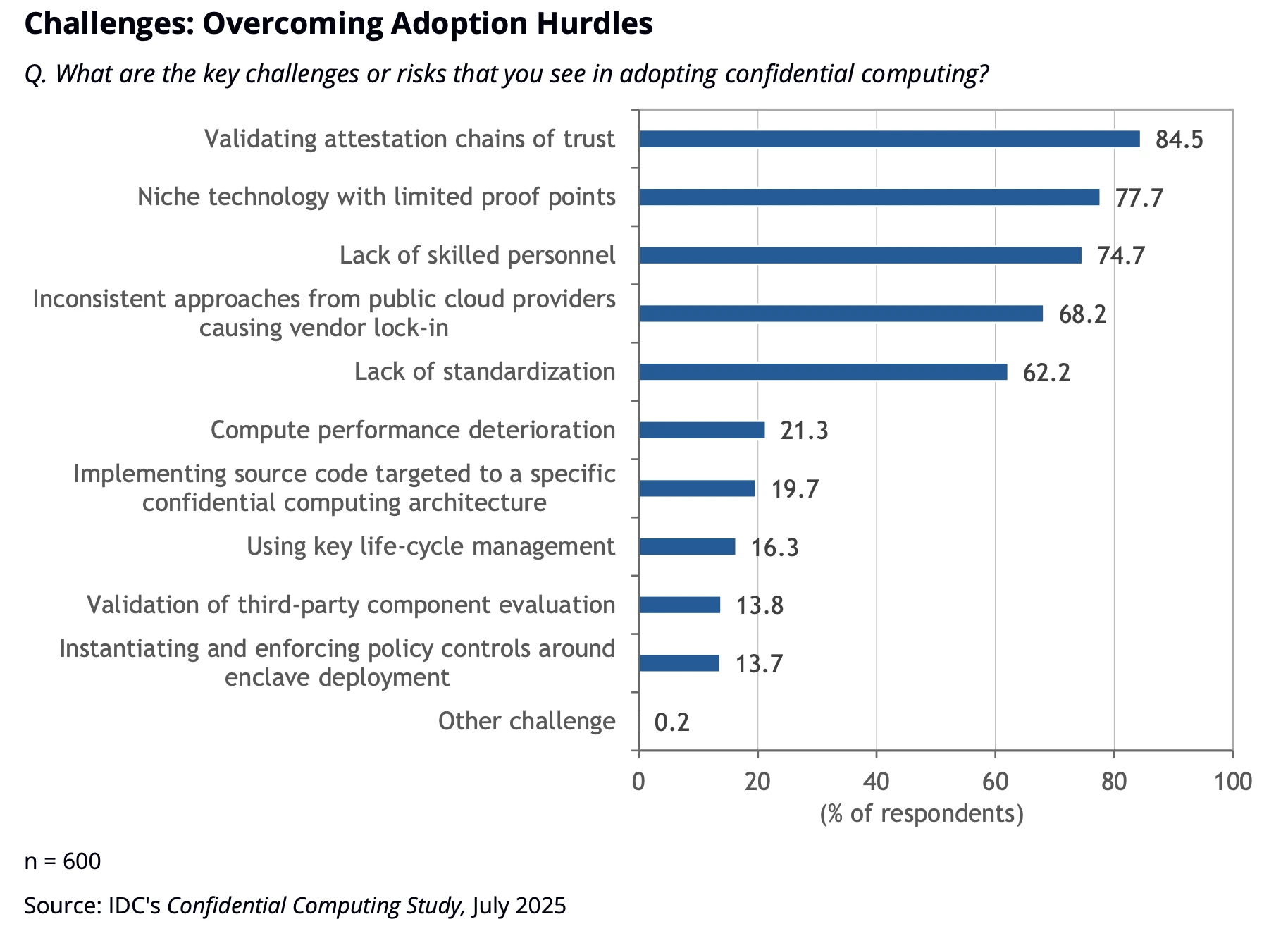
Many confidential computing initiatives stall not because TEEs do not work, but because the organization has not yet turned attestation into a dependable, repeatable security control.
What remote attestation must prove in practice
A production-grade attestation chain needs to support decisions like "should this workload receive keys or data" based on verifiable evidence of:
- Platform authenticity: anchored to a PKI root of trust and endorsement chain.
- TCB level and security posture: patch level, configuration, debug state, revocation status.
- Workload identity: measured state that matches an approved baseline.
- Freshness: protection against replayed evidence.
- Policy enforcement and auditability: deterministic decisions and audit logs.
Why adoption can stall
The core problem is not a missing feature. It is the specialized expertise required to validate and operationalize attestation across heterogeneous platforms, especially when the relying party sits outside the infrastructure boundary.
In practice, a verifier must interpret and validate proof across multiple layers:
- Cryptographic evidence parsing and verification
- Composite attestation claims for hybrid compute (CPU + GPU(s))
- Attestation PKI anchors and endorsement chains
- TCB interpretation across hardware, firmware, and configuration
- Workload measurements and baseline governance
- Relying party verification outside the infrastructure boundary
IDC also highlights the skills gap and the opportunity for managed services and consulting partners to help organizations navigate secure access and compliance as confidential computing adoption scales.
Verifiability as the core security property
A TEE or confidential VM provides an isolated execution boundary. It becomes a security control only when you can prove what is running inside that trusted compute domain and enforce decisions or policies based on that evidence.
CENSUS position and value proposition is:
TEEs and confidential VMs are necessary building blocks, but the objective is continuous verification and enforcement so that keys and sensitive data are released only to workloads in an approved, trusted state.
Practically, this means designing for:
- Policy-driven key release: secrets are released only when evidence satisfies policy.
- Measurement-bound workload identity: stronger than tags, locations, or naming conventions.
- Continuous assurance: resilient to certificate rotation, scaling, and TCB updates.
Securing the application flow
Most sensitive assets are the data, keys, and digital IP moving through a multi-service flow: APIs, orchestration, retrieval, inference, logging, and downstream systems.
A strong starting point is the use case IDC recommends for adopters: securing a RAG pipeline. A secure RAG design should answer questions like:
- When is retrieval context released, and only to which attested inference workload?
- How do we prevent unapproved measurements from receiving secrets?
- What evidence do we log so compliance can verify enforcement?
Cryptellum [5] addresses this security need. It integrates confidential computing into application paths, using attestation to drive access decisions, establish secure sessions, and maintain end-to-end trust across distributed deployments.
DORA accelerating demand with verifiable controls
IDC highlights EU DORA [3][4] as a major adoption driver because it raises expectations for availability, authenticity, integrity, and confidentiality for data at rest, in use, and in transit, and reports that 77% of organizations are more likely to consider confidential computing due to DORA.
The key word is demonstrable. In regulated environments, you need to show:
- which security properties you rely on,
- how you prove them at runtime,
- and how you detect and respond when those properties degrade.
CENSUS solutions in the confidential computing space
CENSUS supports confidential computing adoption as an engineering program focused on turning platform capabilities into impactful security enhancements. We combine Cryptellum with security engineering services to make remote attestation operational, so sensitive data and keys are released only to approved workloads in a verified state, across public cloud, private cloud, on-premises, and edge environments.
1) DESIGN: Confidential Computing Readiness and Use Case Scoping
Identify where data and asset risks exist and what must be proven at systems' runtime.
Deliverables:
- Data-in-use attack surface mapping tied to business flows (AI, RAG, analytics, multi-party collaboration)
- Threat model focused on trust boundaries, privileged access, and lifecycle risks
- Platform and TEE strategy across your target environments
- Initial attestation and policy requirements (what you will verify, what you will enforce)
- Adoption roadmap from pilot to production
2) BUILD: Attestation Control Plane Implementation
Turn attestation into a security control that relying parties can use to establish trustworthiness with remote systems.
Deliverables:
- Attestation verifier design and implementation: trust anchors, evidence validation, freshness, revocation handling
- Composite trust chain validation where needed (including hybrid compute such as CPU plus accelerators)
- Policy model for "approved state" decisions (TCB posture, debug state, measurement baselines)
- SOC/SIEM audit-friendly decision logging (what was verified, what was enforced, when, and why)
3) BUILD: Identity Based Policy Enforcement
Ensure secrets are released across system only when attestation verification passes.
Deliverables:
- Integration with KMS, HSM, IAM, and CI/CD so key release and access decisions are conditional on attestation
- Measurement-bound workload identity and baseline governance (how measurements are produced, approved, and updated)
- Reusable modules / SDKs that combine the three principles: workload identity, key access, session establishment
4) BUILD: Application Data Plane E2EE and Security Hardening
Clients fully control when and how to authorize access to data, without having to trust the intermediate broker systems.
Deliverables:
- Fully featured integration with Cryptellum for confidential AI inference and training
- Reference architectures and implementation for secure RAG and confidential AI agents
- Enforcement points across APIs, orchestration, retrieval, inference, logging, and downstream systems
5) DevSecOps: Managed Deployment and Operations Support
Support cloud, platform, and system security teams adopt, integrate, and operate confidential computing in production.
Deliverables:
- Managed integration services across hybrid environments, including interoperability guidance to reduce operational variance
- Operational blueprints and runbooks for certificate rotation, endorsement chain updates, PKI anchor management, TCB updates, and revocations
- Continuous monitoring and assessment for attestation failures, degraded trust posture, and policy drift, with clear escalation paths and evidence retention
If you operate in a regulated industry, or you need stronger protection for data in use, CENSUS provides the engineering foundation to deploy confidential computing efficiently and at scale. Our guiding principle is remote attestation validation with policy-driven enforcement, so keys and sensitive data are released only to approved workloads in a verified state, with audit evidence that supports compliance and operational assurance.
References
[1] IDC, Unlocking the Future of Data Security: Confidential Computing as a Strategic Imperative, November 2025
https://confidentialcomputing.io/wp-content/uploads/sites/10/2025/11/US53866125.pdf
[2] Confidential Computing Consortium, "New study finds confidential computing emerging as a strategic imperative for secure AI and data collaboration"
https://confidentialcomputing.io/2025/12/03/new-study-finds-confidential-computing-emerging-as-a-strategic-imperative-for-secure-ai-and-data-collaboration/
[3] DORA Level 1 (Regulation EU 2022/2554 – EUR-Lex PDF), Article 9(2) (Protection and prevention)
https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX%3A32022R2554
[4] DORA Level 2 RTS (Commission Delegated Regulation, C(2024) 1532 final – PDF), Article 6 (Encryption and cryptographic controls)
https://ec.europa.eu/finance/docs/level-2-measures/dora-regulation-rts--2024-1532_en.pdf
