Operationalizing Confidential Computing: Verifiable Attestation in Practice
IDC’s November 2025 white paper [1], based on its July 2025 study of 600 global IT leaders, shows that confidential computing has moved beyond early adoption. 75% of organizations are already using it, with 18% in production and 57% piloting, and participants are directly involved in systems that process confidential or regulated data.
Grand Sponsor: 2nd Cyber Intelligence Summit 2026
CENSUS is honored to participate as a Grand Sponsor of the 2nd Cyber Intelligence Summit 2026, held under the theme "Information as Defense: From Everyday Practice to Global Strategy" on February 5 at the Athens Concert Hall.
Thinking Like an Adversary (Developers:Day 2025)
It was an honour to participate and contribute to kariera.gr's Developers Day event. The gathering provided an excellent opportunity for participants to connect, exchange insights, and spark new collaborations.
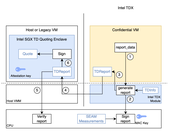
Challenging the Boundaries of Confidential Computing for AI
CENSUS has conducted an in-depth technical evaluation of Confidential AI workloads on Google Cloud Platform (GCP), focusing on the integration of Intel Trust Domain Extensions (TDX) and NVIDIA H100 GPUs within Confidential Virtual Machines (CVMs). The assessment explored whether hardware-based attestation could be extended consistently across both CPU and GPU components and whether a verifiable trust model could be maintained end-to-end. The work was performed on A3 instances, implementing end-to-end attestation flows, validating quote and key hierarchies, and operating under realistic cloud deployment constraints.